Cyber threats such as ransomware, phishing, and supply chain breaches continue to evolve. To stay protected, every business should conduct a cybersecurity audit. An audit highlights gaps in your current systems, evaluates risks, and helps strengthen defences before attackers exploit weaknesses.
Whether you’re a small legal practice or a large enterprise, a structured IT security audit is one of the most effective ways to safeguard sensitive information, meet compliance obligations, and ensure business continuity.
What is a Cybersecurity Audit?
A cybersecurity audit is a comprehensive and formal review of your organisation’s security infrastructure, covering networks, servers, endpoints, and even physical access controls. The objective is simple: reduce the risk of cyberattacks while protecting client data and critical business assets.
During a security audit, your cyber audit team will:
Review existing security policies and procedures;
Assess the effectiveness of firewalls, intrusion detection, and access management systems;
Test compliance with industry regulations and internal standards;
Identify gaps and prioritise remediation steps.
Think of it as a full information security audit, not just checking the technology, but also how people and processes interact with it. Done properly, cybersecurity auditing provides a clear picture of your risk exposure and delivers a roadmap to improve resilience.
Cybersecurity audits focus on 4 core domains: Governance (policies & accountability), Operations (daily security practices), Technology (controls like patching & endpoint security), and Audit’s Role (objectives & scope). They may also extend to Identity & Access Management, Network Security, Data Protection, and Physical Security for full coverage across people, processes, and technology.
Benefits of a Cybersecurity Audit
Carrying out a cybersecurity audit does more than protect your data. A cybersecurity audit improves your security and strengthens business operations. By reviewing policies, systems, and controls, an audit highlights risks and sets the foundation for long-term resilience.
Below are the most important benefits of regular IT security audits.
1. Identify Vulnerabilities
One of the biggest advantages of a security audit is finding weak spots across your IT environment. From outdated software to poor access controls, identifying these gaps early means you can fix them before attackers exploit them. This proactive approach reduces the likelihood of costly breaches.
2. Strengthen Protection
After vulnerabilities are detected, stronger safeguards are applied. A structured information security audit helps ensure your systems are prepared for common threats such as ransomware, phishing, and malware. Reinforcing your defences makes day-to-day operations safer and more reliable.
3. Regulatory Compliance
Many industries face strict rules around cybersecurity audits and compliance. For example, legal firms must uphold client confidentiality, while financial services need to follow PCI DSS or APRA guidelines. Regular cybersecurity audits ensure your business remains compliant, avoids penalties, and maintains client trust.
4. Improved Incident Response
A well-run cyber audit reviews how effectively your team can detect, contain, and recover from an incident. This evaluation helps refine response procedures so you can limit downtime and reduce financial and reputational damage in the event of a breach.
5. Risk Management
A thorough IT audit cybersecurity assessment gives clarity on the threats most likely to affect your organisation. With this knowledge, decision-makers can prioritise risks, allocate resources more efficiently, and protect high-value assets without unnecessary costs.
6. Stakeholder Confidence
Regular cybersecurity audits build confidence among clients, investors, and partners. Demonstrating that you take data protection seriously enhances your reputation and reassures stakeholders that sensitive information is safe.
7. Continuous Improvement
Cyber risks evolve quickly, and so must your defences. Ongoing assessments ensure that policies, controls, and technologies remain up to date. A cycle of regular security audits keeps your business a step ahead of cybercriminals and aligned with best practices.
How Often Should You Perform a Cybersecurity Audit?
The frequency of a cybersecurity audit depends on your industry, compliance rules, and the sensitivity of your data. High-risk sectors, like law, finance, and healthcare, should schedule a formal IT security audit every 12–18 months to mitigate threats and meet regulatory standards.
Audits should also follow major system upgrades, infrastructure changes, or security incidents to confirm controls are still effective and gaps are addressed.
Cyber Security Audit Checklist: When to Schedule the Audit
- High-risk industries: every 12–18 months
- After major IT changes: infrastructure, cloud, or software rollouts
- Following a breach or attack: to test response and patch gaps
- Regulatory deadlines: PCI DSS, ISO 27001, APRA compliance
- Best practice: at least one cybersecurity auditing cycle every two years
Regular cybersecurity audits reduce breach risks, maintain compliance, and assure clients and regulators that data protection is a priority.
How to Perform a Cybersecurity Audit
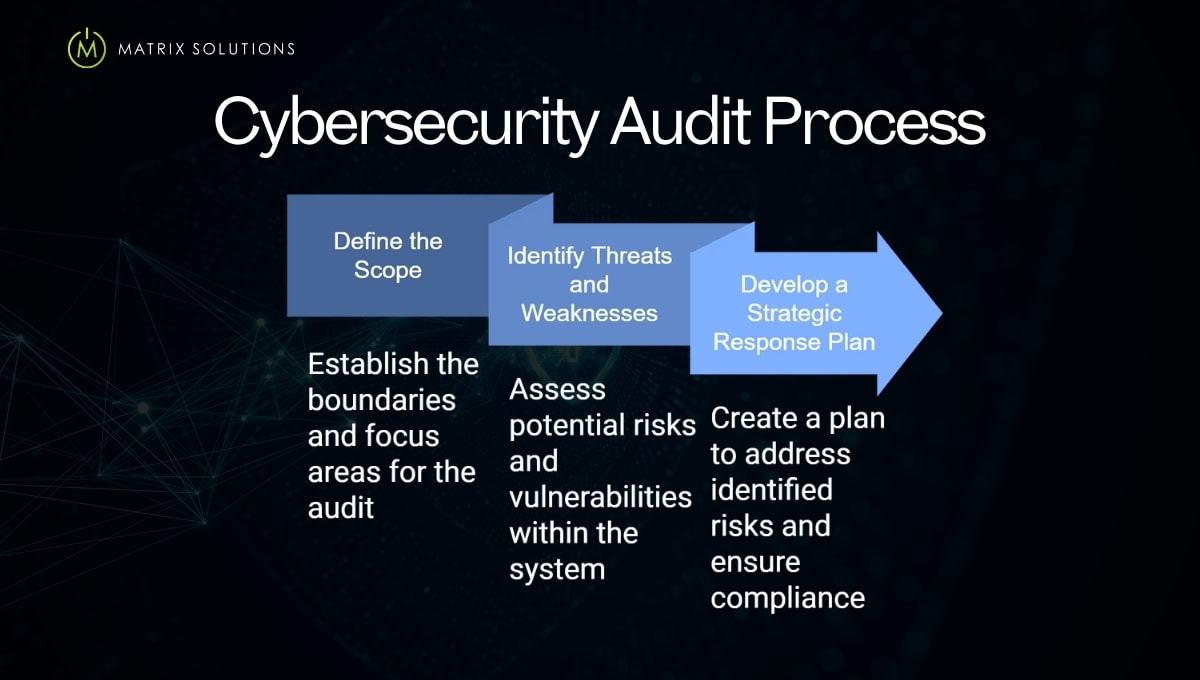
Conducting a cybersecurity audit requires a structured, step-by-step approach. The goal is to thoroughly review systems, policies, and controls so that your organisation has a clear picture of its security posture.
Below are the key stages of an effective IT security audit.
1. Define the Scope
Start by setting clear boundaries for the audit. Decide which systems, networks, and data will be reviewed. Depending on your needs, the scope may cover your entire infrastructure or focus on specific areas such as cloud platforms, databases, or compliance controls.
Key areas to include:
- IT infrastructure: Hardware, software, and network resources
- Sensitive data: How information is stored, transferred, and protected
- Physical security: Access restrictions for offices and server rooms
- Security policies: Existing frameworks and user policies
- Compliance obligations: Industry standards such as PCI DSS, ISO 27001, or APRA.
2. Identify Threats and Weaknesses
Next, evaluate internal and external risks that could affect your business. This part of the information computer security audit highlights gaps that attackers could exploit.
Common vulnerabilities include:
- Distributed Denial of Service (DDoS) Attacks are disrupting availability.
- Malware and ransomware targeting critical data
- Shadow IT from unapproved devices or apps
- Social engineering, such as phishing, baiting, pretexting, and business email compromise.
- Stolen credentials exposing systems
- SQL injections targeting web applications
- Zero-day flaws that remain unpatched.
3. Develop a Strategic Response Plan
Once risks are identified, the cyber audit team should create an action plan that prioritises fixes and supports compliance. A strong response plan balances immediate protection with long-term resilience.
It should cover:
- Risk prioritisation: Addressing the most urgent vulnerabilities first.
- Business continuity: Recovery procedures after a disruption
- Incident management tools: For detection, prevention, and response.
- Communication strategy: Staff training and response protocols during incidents.
Step 4: Execution & Follow-Up
Finally, determine how the audit will be carried out and ensure improvements are sustained over time. This stage focuses on choosing the right audit method, verifying remediation efforts, and maintaining ongoing visibility into your security posture.
Key actions to include:
- Choose Audit Type:
- Internal audits → cheaper, more frequent, but less objective.
- External audits → independent, unbiased, trusted for compliance (e.g., SOC 2).
- Schedule Follow-Ups: Verify fixes worked and address new threats.
- Use Continuous Monitoring: Automated tools provide real-time visibility between audits and help manage risk proactively.
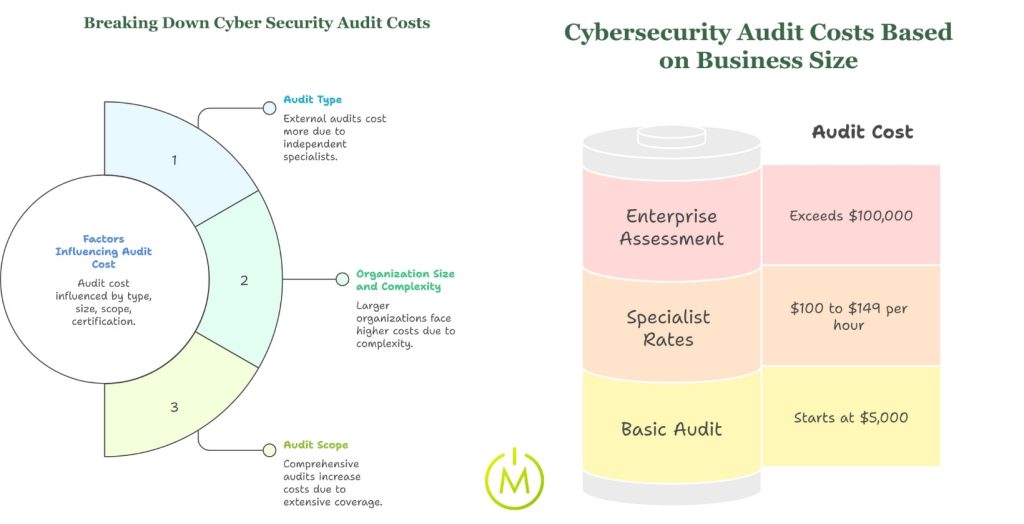
How Much Does a Cybersecurity Audit Cost?
The cybersecurity audit cost depends on the size of your organisation, the complexity of your IT systems, and the level of detail required.
Typical Cost Ranges
Here is a breakdown of the typical costs:
- Basic Small Business Audits: Costs for a basic audit for a small business start at around $5,000.
- Enterprise Assessments: For larger enterprises, the cost of an assessment often exceeds $100,000.
- Hourly Rates: External specialists typically charge between $100 and $149 per hour for their services.
Important financial consideration: Post-audit remediation costs often exceed the initial expense of the audit itself. These costs are incurred when fixing the vulnerabilities and gaps identified in the final audit report.
For tailored advice, contact Matrix Solutions. Our team delivers comprehensive cybersecurity services designed to match your budget, compliance needs, and risk profile.
Factors Influencing Cyber Security Audit Cost
The total cost of an audit is influenced by audit type, organization size, scope, and certification requirements.
1. Audit Type (Internal vs External)
The type of audit is a primary cost driver.
- External audits cost more because they involve independent specialists, longer timelines, and compliance certification requirements. Third-party specialists perform external audits.
- Internal audits are less expensive and can be repeated more often, but may lack independence. An organization’s own employees conduct Internal Audits.
2. Organization Size and Complexity
Larger organizations with complex IT infrastructures face higher costs. Multiple networks, endpoints, and databases require more resources, more testing, and longer audit times.
3. Audit Scope
The scope determines audit depth and cost.
- Comprehensive audits (annual, full coverage) require more time and resources, increasing cost.
- Targeted audits (quarterly or compliance-specific) are narrower and less expensive.
- Standards-driven audits (PCI DSS, GDPR, ISO 27001) typically increase costs compared to general risk assessments.
Cost of Professional Certification (for Auditors)
It is important to distinguish the cost of an audit service for an organization from the cost of a professional certification for an individual auditor. The ISACA Cybersecurity Audit Certificate exam is intended for professionals seeking to prove their expertise in the field. The fees for the ISACA Cybersecurity Audit Certificate exam are:
- ISACA Member: US $259
- Non-Member: US $299
How Long Does an IT Security Audit Take?
The timeline for an IT security audit varies with its scope and depth. A smaller business may complete an audit in around one week, while larger organisations with multiple systems and compliance requirements may need several weeks for a full review.
Key factors that influence duration include:
- The size of your IT environment
- The number of systems under review
- Specific information security audit requirements for your industry.
To understand the expected timeline for your business, reach out to us for a consultation. Our cyber audit team will provide a clear plan based on your infrastructure and compliance obligations.
How Do We Conduct a Cybersecurity Audit?

With more than 27 years of experience, Matrix Solutions delivers tailored cybersecurity audits for law firms, financial services, insurers, and real estate businesses. As a trusted IT partner in Sydney, we make sure every audit follows compliance requirements and recognised industry standards.
- Initial Consultation: We begin with a consultation to understand your environment, data sensitivity, and security concerns, ensuring the cybersecurity audit scope matches your needs.
- Risk Assessment: Our team performs a full IT security audit, reviewing networks, access controls, cloud platforms, and data protection. We also check compliance through structured information security audit measures.
- Actionable Recommendations: After the audit, we provide a detailed cybersecurity audit report with prioritised steps to address vulnerabilities and strengthen resilience.
- Ongoing Support: Security isn’t a one-time task. Our cyber audit team provides ongoing monitoring, updates, and support to help your systems adapt as threats evolve.
Ready to protect your business with a state-of-the-art cybersecurity audit?
Cyber Security Audit Services
Contact Matrix Solutions today to schedule your cybersecurity audit and take the first step towards enhanced cyber protection.
Book Your Free Consultation



