Australian SMEs, particularly law firms, are prime targets for cyberattacks that exploit everyday applications such as browsers, Office tools, and PDF readers. These attacks often utilise macros, scripts, or outdated plugins to breach systems silently.
User Application Hardening is a non-negotiable defence that stops these exploits before they execute. As a core pillar of the ACSC’s Essential Eight, it prevents malicious code from running in trusted environments, making it essential for any business aiming to meet modern security standards.
Key Insights at a Glance
User application hardening disables risky app features to block malware and macros.
It’s a core part of the ACSC Essential Eight cybersecurity framework.
Focus areas: browsers, Office apps, and PDF readers.
Key actions: disable Flash, Java, macros, and auto-run features.
Tools like Intune, GPO, and SIEM enforce policies.
Ideal for SMEs and law firms handling sensitive data.
What is User Application Hardening?

User Application Hardening is the process of disabling or restricting exploitable features within commonly used software. It reduces attack exposure by removing high-risk components, such as macros, JavaScript, Flash, or browser ads.
This proactive control strengthens endpoint security by protecting user-facing apps where threats typically enter. For businesses, it limits breach pathways without disrupting daily operations.
Why Application Hardening Matters for Businesses’ Security
Application hardening significantly reduces the attack surface by eliminating unused or high-risk features within everyday software. This proactive control removes common entry points exploited by attackers, such as phishing vectors, malicious documents, and drive-by downloads, before they can cause harm. By securing frontline tools like email clients, web browsers, and productivity apps, businesses can prevent breaches at the user level without relying solely on reactive security measures.
Why Application Hardening is a Pillar of the ASD Essential Eight
Application hardening is a core requirement of the Australian Cyber Security Centre’s (ACSC) Essential Eight (ASD E8) framework. Mandated at all maturity levels, this control is critical for any organisation seeking compliance. It ensures commonly exploited features, such as macros, Flash, and web advertisements, are disabled by default, significantly reducing exposure to ransomware, phishing, and document-based malware.
Which Business Applications Require Hardening?

Under the Essential 8 user application hardening strategy, attackers most commonly exploit trusted software that employees use daily. These widely used apps are often overlooked but are high-risk entry points.
The following categories require immediate focus on hardening.
Web Browsers (Chrome, Edge, Firefox)
Web browsers are among the most targeted applications in enterprise environments. Their ability to run scripts, display ads, and support extensions makes them prime vectors for malware, phishing, and drive-by attacks. Browser hardening minimises these risks by disabling insecure features and enforcing strict security configurations.
Recommended Hardening Actions:
- Disable legacy technologies like Java and Flash, which are no longer supported and pose known vulnerabilities
- Retire or restrict Internet Explorer 11, which lacks modern security standards.
- Use DNS filtering or reputable ad blockers to block ads and pop-ups that can carry malicious payloads.
- Prevent the installation of unapproved browser extensions, which may leak data or introduce vulnerabilities.
- Enforce HTTPS-only mode to ensure secure communication and prevent downgrade attacks.
Microsoft Office (Word, Excel, Outlook)
Microsoft Office applications are a frequent target for attackers due to their support for macros, ActiveX controls, and OLE (Object Linking and Embedding). These features are often exploited to deliver malware through seemingly legitimate documents, such as invoices, contracts, or legal notices, triggering malicious code execution when they are opened.
Recommended Hardening Actions:
- Block all macros from the internet to prevent remote code execution.
- Enable Protected View for files originating from unknown or unsafe locations.
- Restrict or disable add-ins and OLE objects to minimise embedded code risks.
- Use Group Policy to enforce macro security settings across the organisation.
- Limit execution of risky file types through application control or security baselines.
PDF Software (Adobe Acrobat, etc.)
PDF files are often perceived as safe, but they’re a common vehicle for malware, particularly in phishing attacks, due to support for embedded scripts, malicious links, and exploit kits. Misconfigured PDF readers, especially Adobe Acrobat, are a frequent entry point for threat actors.
Recommended Hardening Actions:
- Disable JavaScript execution within PDF readers to prevent script-based exploits
- Enable Protected Mode (sandboxing) to isolate PDF processes from the host system.
- Block auto-opening of embedded files, which may trigger malware without user action.
- Remove support for 3D content and multimedia, which increases the attack surface.
- Prevent auto-launch of embedded files or links to stop drive-by infections.
Why This Matters for Australian Businesses
Recent incidents in sectors like healthcare, legal, and education have shown how attackers exploit trusted applications to gain access to sensitive data. For example, high-profile breaches, such as the Medibank and Latitude Financial cases, underscore the importance of securing commonly used tools like Office and PDF software before threats escalate. Hardened applications can act as a frontline filter against such attacks.
Application Hardening Across the Essential Eight Maturity Levels
The Essential 8 maturity model defines a progressive path to stronger security. It uses Maturity Levels 1 to 3 to guide organisations from basic implementation to complete control, visibility, and resilience.
Below is a level-by-level breakdown of what’s required:
Maturity Level One: Baseline Controls
At Maturity Level One of the Essential 8 framework, organisations should implement foundational browser hardening measures. Focus on disabling outdated plugins, such as Flash and Java, blocking web-based ads and pop-ups, and enforcing secure defaults through Group Policy or mobile device management (MDM) tools. These baseline controls reduce exposure to common browser-based threats and lay the groundwork for higher security maturity.
Maturity Level Two: Expanding Coverage
At Maturity Level Two of the ASD Essential 8, security hardening extends beyond browsers to include Microsoft Office and PDF applications. Organisations should block all macros and disable ActiveX controls in Office apps, while applying script execution restrictions in PDF readers to prevent embedded attacks. Use enterprise tools like Microsoft Intune or Endpoint Manager to centrally deploy and enforce these configurations across all endpoints, ensuring consistent protection.
Maturity Level Three: Logging & Restrictions
At Maturity Level Three of the ASD Essential 8, organisations must implement advanced hardening measures and enhance system visibility. This includes disabling outdated frameworks such as .NET 3.5 and PowerShell 2.0, which are often targeted in modern attacks. To support detection and response, enforce centralised logging using tools like SIEM solutions, Sysmon, or Windows Event Viewer to monitor and alert on unauthorised changes across the environment.
How to Implement User Application Hardening in Your Organisation
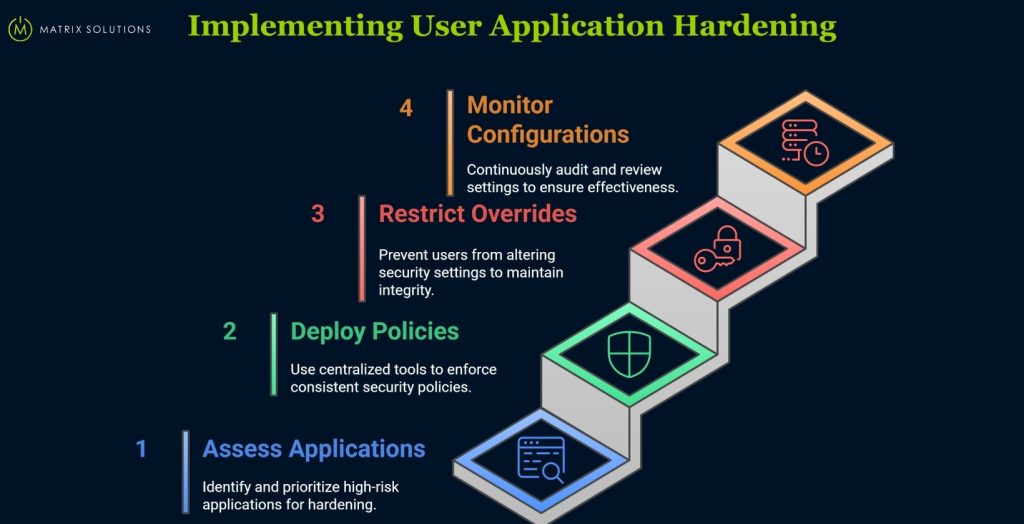
According to the essential 8 implementation guide, user application hardening should follow a phased, structured rollout to minimise disruption and ensure enforcement.
Below is a high-level checklist organisations can follow to implement this control effectively.
Step 1. Assess & Prioritise Applications
The Essential 8 guidelines recommend beginning with a full inventory of all user-facing applications across your organisation. Assess each application’s risk based on factors like usage, exposure to external content, and past vulnerabilities. Prioritise high-risk categories, such as web browsers, email clients, and document-handling tools, for the initial phase of your application hardening rollout.
Step 2. Deploy Policies via Centralised Tools
Deploy application hardening policies consistently across your environment using centralised management tools like Microsoft Intune or Group Policy Objects (GPOs). This approach ensures every endpoint adheres to a unified security baseline, reducing configuration drift and minimising manual effort.
Examples of centralised policy tools:
- Microsoft Intune: Cloud-based enforcement for modern, distributed environments
- Group Policy Objects (GPO): Centralised control for on-premises Windows systems
Step 3. Restrict User Overrides and Bypass Paths
To preserve a consistent security baseline, application hardening policies must be locked down to prevent user tampering or rollback. Allowing overrides introduces configuration drift, weakens defences, and increases the risk of compromise. Enforcing non-negotiable controls ensures that critical security settings remain intact across all endpoints.
Recommended restriction methods:
- Enforce registry key permissions to prevent unauthorised modifications
- Apply user-specific Group Policy restrictions to limit changes at the user level
- Remove access to Control Panel and PowerShell to block common bypass paths
- Disable the Local Group Policy Editor to prevent local policy changes
Step 4. Audit, Monitor, and Review Configurations
Continuous monitoring is essential to ensure application hardening controls remain effective and uncompromised. Configure centralised logging to capture enforcement outcomes, detect policy bypass attempts, and maintain real-time visibility across all endpoints. Logging also supports compliance reporting by creating a verifiable audit trail.
Recommended tools:
- Windows Event Viewer: Native event logging for basic visibility
- Sysmon: Advanced telemetry for process, network, and file activity
- SIEM platforms like Splunk or Microsoft Sentinel: Centralised alerting, correlation, and compliance dashboards
Policy-Based vs Manual Application Hardening Approaches
Application hardening can be implemented using two approaches: policy-based and manual. Policy-based hardening is centralised and scalable, while manual methods are used for isolated systems.
Each has trade-offs, which we explore in the sections below.
Centralised Policy Enforcement with Group Policy or MDM
Centralised tools like Microsoft Intune, Group Policy Objects (GPOs), and mobile device management (MDM) platforms enable consistent and scalable policy deployment across all endpoints. These platforms support MDM policy enforcement by automating configuration, enforcing compliance, and reducing manual errors.
Key benefits of centralised policy enforcement:
- Standardised settings across devices
- Automated, zero-touch enforcement
- Scalable for remote or hybrid teams
- Improved auditability and rollback tracking
Many Australian SMEs also work with managed service providers (MSPs) who use local tools such as Telstra Adaptive Security, Secureworks ANZ, or Kaseya VSA, alongside Microsoft Intune or GPO.
Manual Hardening Techniques
Manual application hardening may still be necessary for legacy systems or standalone devices that lack mobile device management (MDM) support. However, this approach introduces significant challenges most notably inconsistent configurations, limited visibility, and increased administrative overhead.
Key risks of manual hardening:
- Misconfigured settings due to human error or oversight.
- No audit trail or tamper detection, making it difficult to verify integrity.
- Inability to enforce policies remotely, leaving gaps in enforcement.
- Difficult to scale and maintain, especially in dynamic environments.
When to Use Hybrid Approaches
Hybrid hardening approaches are useful when certain systems can’t be managed through central tools alone. This typically occurs in environments with legacy applications, operating system fragmentation, or during transitional IT projects. Combining both methods ensures no endpoint is left exposed.
Common scenarios for hybrid approaches:
- Legacy apps are incompatible with Intune or GPO
- Temporary systems outside domain control
- Mixed OS environments (Windows/macOS/Linux)
- Migration projects involving phased deployments
Unsure about your application hardening? Contact Matrix Solutions for a tailored security assessment and scalable, standards-aligned configurations.
Key Benefits of Strong Application Hardening Policies
The key benefits of strong application hardening policies are listed below:
- Blocks Exploits at Runtime: Stops malware and scripts before execution, reducing drive-by and macro-based attacks.
- Reduces Phishing Success Rates: Disabling macros in Office and PDFs removes common payload paths in phishing emails.
- Strengthens Compliance Posture: Aligns with ISO 27001 and Essential 8 application control, easing audits in regulated sectors.
- Maintains Operational Continuity: Prevents disruptions to legal workflows, protecting client deadlines and document integrity.
- Lowers Incident Response Overhead: Fewer threats reach endpoints, reducing alerts, triage, and remediation work.

How Application Hardening Fits Into Broader Endpoint Security
User application hardening enhances endpoint security by blocking high-risk actions, such as script execution, before antivirus or EDR tools can respond. It reduces reliance on urgent patching and enforces consistent policies via MDM tools like Intune or GPO. As part of a layered defence model, it complements rather than replaces traditional controls.
Layered Endpoint Protection: How Hardening Fits In
Control Type | Primary Role | How Hardening Compliments It |
Antivirus(AV) | Detects known threats | Blocks scripts/macros before they’re scanned |
EDR | Monitors suspicious behaviour | Prevents exploit execution before detection triggers |
Patch Management | Fixes software vulnerabilities | Closes common exploit paths before patching is applied |
Device Management | Enforces configurations | Delivers hardening rules uniformly across all endpoints |
Common Mistakes to Avoid During Application Hardening
Here are common mistakes to avoid when applying Essential 8 application hardening.
Mistake: Allowing users to override settings
→ Fix: Enforce read-only Group Policy Objects (GPOs) and lock registry keys to maintain control.
Mistake: Hardening apps without testing configurations
→ Fix: Always pilot changes in a dev or staging environment before applying across the business.
Mistake: Inconsistent enforcement across endpoints
→ Fix: Use centralised tools like Microsoft Intune or GPO to ensure consistent application across all devices.
Mistake: Limiting hardening to just browsers
→ Fix: Audit all user-facing software, Office, PDF readers, and browsers to align with the Essential 8 application control scope.
Mistake: Not enabling logging or monitoring
→ Fix: Integrate application control events with a SIEM to detect policy violations in real time.
How to Choose the Right Hardening Tools
Choosing the right hardening tool depends on your firm’s size, compliance requirements, and IT capacity. Use this framework to compare commercial tools, open-source options, and key evaluation criteria.
Commercial Tool Examples (Ivanti, Microsoft Intune, etc.)
Commercial hardening tools offer automation, visibility, and consistent policies, ideal for SMEs. Microsoft Intune excels in Intune application hardening with native cloud integration.
Below are key tools to consider, depending on your infrastructure and compliance needs.
- Microsoft Intune → Best for Microsoft 365/cloud environments → Cloud-based policy deployment and integration with Defender
- Ivanti Security Controls → Suited for hybrid enterprises → Combines patch management with hardening profiles
- ManageEngine Endpoint Central → Ideal for SMEs → GUI-based config control, reporting, and asset inventory
- Group Policy Objects (GPO) → On-premise Windows networks → Fine-grained control over hardening and lockdown policies
Open-Source Tool Examples
Open-source tools support user application hardening for teams with strong technical skills and limited budgets. They offer flexibility but less automation than commercial solutions.
- CIS-CAT Pro → Benchmarks configs against CIS standards
- Free, compliance-focused scanning
- Limited automation; manual analysis
- Best for Windows & Linux
- OVAL → Automates vulnerability detection
- Detailed, scalable checks
- Requires scripting knowledge
- Ideal for mature security teams
- OpenSCAP → Scans and enforces policies
- Great for Linux/Unix
- Setup complexity: no GUI
- Fits Linux-centric environments
Key Evaluation Criteria
When selecting a hardening tool, consider the following key factors to ensure it aligns with your environment and security objectives.
- Scalability: Can the tool efficiently manage 10 to 1,000+ endpoints?
- Reporting: Does it provide clear logs, enforcement status, and audit trails?
- Usability: Is the interface intuitive for IT teams with limited time?
- Cost: Is the pricing model sustainable and worth the operational ROI?
- Integration: Does it work with existing MDM, EDR, or SIEM platforms?
Why Partner with Matrix Solutions for Application Hardening?

Matrix Solutions has over 27 years of IT experience, helping Australian SMEs, particularly those in the legal sector, implement user application hardening aligned with the Australian Government’s Essential Eight. We deliver tailored, audit-ready strategies that strike a balance between compliance, risk, and operational needs.
Why clients trust Matrix:
- Legal-sector expertise: Trusted by law firms for our deep domain understanding
- Essential Eight integration: Support across Maturity Levels 1–3, including application control
- Flexible deployments: Expertise in Intune, GPO, and hybrid setups
- Compliance-focused: ASD-aligned configurations, ready for audits and assessments
FAQs About User Application Hardening
Are web browsers hardened using ASD?
Yes, web browsers are hardened using ASD guidelines under the Essential Eight. ASD recommends disabling Flash, Java, and unapproved plugins to reduce exploit risks. Browser hardening is a core part of user application hardening.
Is application hardening the same as patching?
No, application hardening is not the same as patching. Patching fixes known vulnerabilities; user application hardening disables risky features (e.g. macros, scripts) that attackers often exploit, even in up-to-date software.
Can user application hardening hurt employee productivity?
User application hardening can negatively impact productivity if not implemented. When implemented correctly, it protects systems without disrupting essential workflows. Testing configurations and applying exceptions prevent unnecessary disruptions.
Secure Your Applications, Secure Your Business
User application hardening is essential for SME cybersecurity, not optional. As part of the Essential Eight, it blocks attacks at the application layer, where most threats enter. Hardening protects your firm’s systems, clients, and compliance posture with measurable controls.
Unsure about your application hardening maturity? Contact Matrix Solutions for a tailored security assessment and scalable, standards-aligned configurations.




